Resources
Empowering Knowledge, Building ResilienceAt Maverick Gardner Information Technology & Solutions, we believe informed clients make stronger organizations.
Our Resources page provides tools, insights, and guidance to help you navigate cybersecurity, compliance, and IT management with confidence
Guides & Whitepapers
Gain practical knowledge to help your business stay secure, compliant, and ahead of evolving industry standards.

ISO 27001:2022 Readiness Guide
A Practical Roadmap to Certification
Learn how to prepare your organization for ISO 27001:2022. This guide breaks down each requirement—from risk assessments to audit preparation—and offers actionable steps for implementation.
Key Takeaways:
Understand core ISO 27001 controls
Build an internal compliance roadmap
Streamline audits with evidence mapping
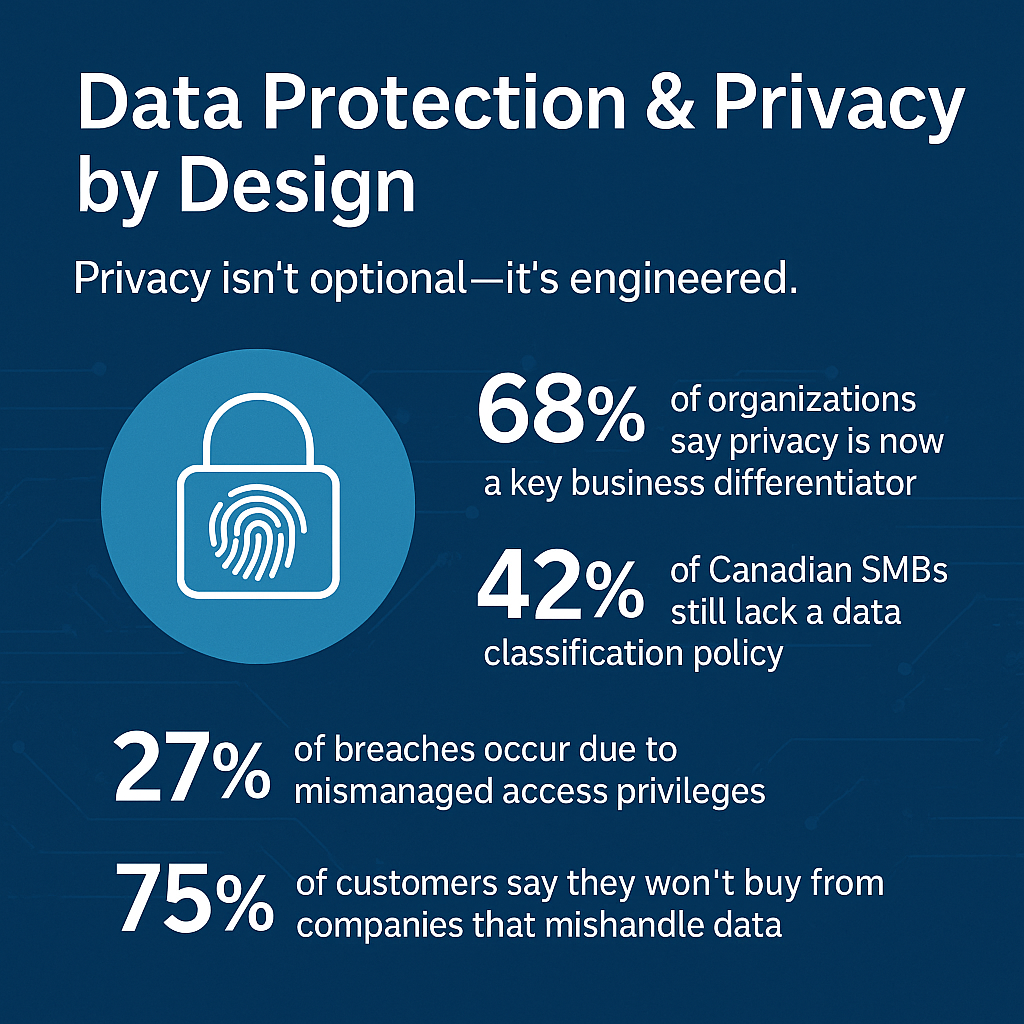

Cybersecurity for Canadian SMBs
Small and medium-sized organizations face increasing threats but often lack enterprise-level defenses. This whitepaper outlines cost-effective, scalable cybersecurity strategies that strengthen your resilience.
Inside:
2025 threat landscape overview
Best practices for endpoint and cloud security
Real-world examples of SMB breach prevention

Compliance-as-a-Service
Integrating Policy, Technology & Trust
Compliance can be complex—but it doesn’t have to be. Learn how Maverick Gardner’s Compliance-as-a-Service framework unifies risk management, monitoring, and reporting into one continuous solution.
Discover:
Automated compliance monitoring
Simplified audit readiness
Reduced risk and administrative burden

Posts
Cybersecurity & Compliance Facts
43% of cyberattacks target small and mid-sized businesses, yet only 14% are prepared to defend themselves.
The average cost of a data breach in Canada reached $7.3 million CAD in 2024 (IBM Security).
Human error causes nearly 82% of data breaches, emphasizing the importance of employee awareness training.
Companies with an incident response plan reduce breach costs by an average of $1.5 million CAD.
ISO 27001:2022 is the leading global standard for information security management — adopted by more than 50,000 organizations worldwide.
Businesses that maintain ISO 27001 certification experience 30% fewer security incidents on average.
Compliance automation can cut manual audit preparation time by up to 60%.
Canadian SMBs are now the top ransomware targets, with phishing as the leading attack vector.
90% of organizations that adopt a cybersecurity framework (like ISO 27001 or NIST) report improved client trust and better vendor relationships.
The average downtime after a ransomware attack for Canadian firms is 23 days — often costing tens of thousands in lost productivity.
Business & IT Resilience Facts
Managed IT Services can reduce total IT operating costs by 25–40% compared to internal management.
Cloud adoption among Canadian SMBs has grown to over 80%, but misconfigurations remain one of the top security risks.
Regular data backups and disaster recovery testing can reduce downtime risk by 96% during incidents.
Employee cybersecurity training reduces phishing success rates by up to 70% within six months.
Zero-trust architecture is now recommended for all Canadian government vendors handling sensitive data.
Compliance-as-a-Service (CaaS) Insights
Organizations that outsource compliance to managed service providers report 50% faster audit completion.
CaaS solutions help meet multiple frameworks simultaneously — including ISO 27001, NIST, SOC 2, and GDPR.
Companies with proactive compliance programs are twice as likely to win contracts in regulated sectors (e.g., defense, utilities).
Automated compliance monitoring provides real-time visibility, reducing manual reporting errors by over 80%.
CaaS delivers predictable costs and continuous assurance, making compliance sustainable rather than seasonal.
Multimedia Resources
Explore our collection of videos and webinars covering IT strategy, cybersecurity, compliance, and managed services — designed to help your organization stay secure, informed, and future-ready.









